How to Increase Your Password Strengths in 5 Easy Steps!
Using strong passwords that combine uppercase and lowercase letters, numbers, and special characters is one of the best ways to ensure password strength. Other best practices for password security include avoiding the use of personal information in passwords and changing passwords frequently.
Best Practices for Increasing Password Strength
- A password with a minimum of 12 characters. Additionally, it might contain some unique characters, such as the dollar sign ($), percent symbol (%), or exclamation mark (!).
- The style of passwords should be different, complex, and illogical. They should be made up of a combination of upper- and lower-case letters, numbers, and symbols, and should not contain dictionary words from any language or be related to anything that could be guessed. They should also not be sequences from a keyboard like “qwerty” or “zxcvb.”
- Do not reuse passwords. It should be against the law for employees to use the same password for both their personal and business accounts.
- Change it after the other person is done using it if you ever need to reveal your password.
- Password rotation, often known as password resetting, is the practice of changing passwords frequently. Depending on the age, usage, and security significance of the password, the frequency of rotation should change. For instance, a basic user account password might only need to be changed every 60 days, a practice that can be compelled by password expiration. On the other hand, superuser passwords and other highly privileged ones should be changed frequently, including one-time passwords (OTPs) for your most sensitive accounts after each usage.
What is a PASSWORD and why do we need it?
Imagine you own a home and need privacy. You would begin by installing locks on the doors and making sure the keys are kept in a secure location. In other words, a password is a set of characters used to distinguish between an authorized user and a process. Or, to put it another way, a password is used to create identification or provide access to a resource.
The confidentiality of a password is presumed. Those characters are used to authenticate access to the safeguard digital system which is known as a password, sometimes abbreviated as PW or PWD. The use of passwords makes it possible to restrict access to computers and data to those who have been given permission to view or use them. A username or other kind of authentication is typically used in conjunction with a password.
Is it recommended to use single passwords for all websites?
You want to develop a password that is not just strong but also distinctive because passwords are frequently your first line of defense when it comes to protecting your information from online dangers. Credential stuffing can occur when a user uses the same password for numerous accounts. When a website’s login credentials have been previously stolen, hackers can “push” those credentials into other websites until they find a match. This practice is known as credential stuffing.
Take the case when your online bank account and account for online shopping both used the same password. In the event that a cybercriminal gains access to your shopping account, where your payment information is maintained, they would be able to determine which bank you use and have the login information they need to access it.
If the password used on one website that you visit is also used on another, the hacker will have an easier time accessing the other accounts. Therefore, it is less probable that several accounts will be hacked if you use different passwords for each website you visit.
What are the tools for Password Management?
The number of personal passwords a person must manage could be in the dozens or even the hundreds. This number may even be higher in organizations, and it also includes embedded passwords in software. When left to humans, password practices are typically not adhered to due to the overwhelming number of passwords to manage. Malware and hacker exploits can then be made possible by poor password hygiene.
Although it is not humanly possible to create and change passwords using optimal guidelines, password management software can automate this process.
Software programs called password managers to uphold recommended procedures for creating and safeguarding passwords (such as by using encryption). The user can instruct the password manager to automatically retrieve the proper password from a database and authenticate into a system or software by filling out a form by using a master password or key. The desktop, the cloud, or a browser can all host password managers.
To manage login information for corporate privileged accounts, a particular subclass of password managers called “Enterprise Password Managers” or “Privileged Password Managers” is employed.
Can you guess the most common password?
According to a list of the top, most popular passwords over the past year, “123456,” “qwerty,” and “password” are among the 25 most often used passwords. Over 50% of users use a password from the Top 25 list, according to research done by password manager Keeper using 10 million passwords exposed in data breaches.
However, the entries “18atcskd2w” and “1q2w3e4r5t” are less expected. Why? The culprits are spambots. According to security blogger Graham Cluley, these are the passwords that bots use to create hordes of false accounts on forums and in comment sections so they can post those obnoxious spam advertisements. If you’ve ever had to pass a quick test to “prove you are human” before your account can be created.
- 123456
- 123456789
- qwerty
- 12345678
- 111111
- 1234567890
- 1234567
- password
- 123123
- 987654321
- qwertyuiop
- mynoob
- 123321
- 666666
- 18atcskd2w
- 7777777
- 1q2w3e4r
- 654321
- 555555
- 3rjs1la7qe
- 1q2w3e4r5t
- 123qwe
- zxcvbnm
- 1q2w3e
How do they design future passwords?
Users could eventually completely do away with passwords in order to access services, and instead utilize alternatives like the speech recognition Siri app or the Authenticator apps, which use fingerprint or facial recognition technology to let you log in securely.
Users can log in using a security key that physically plugs into their computer and has encryption specific to them and their device, or with a verification code that is given to their phone or email.
Microsoft’s vice president of identity, Joy Chik, noted in a blog post published in September that while additional security measures like two-factor authentication have helped to increase user account security in recent years, hackers can still discover ways to circumvent them. She added, “Passwords are insecure as long as they are still a factor in the equation.”
We list only some of the numerous advancements you will observe as
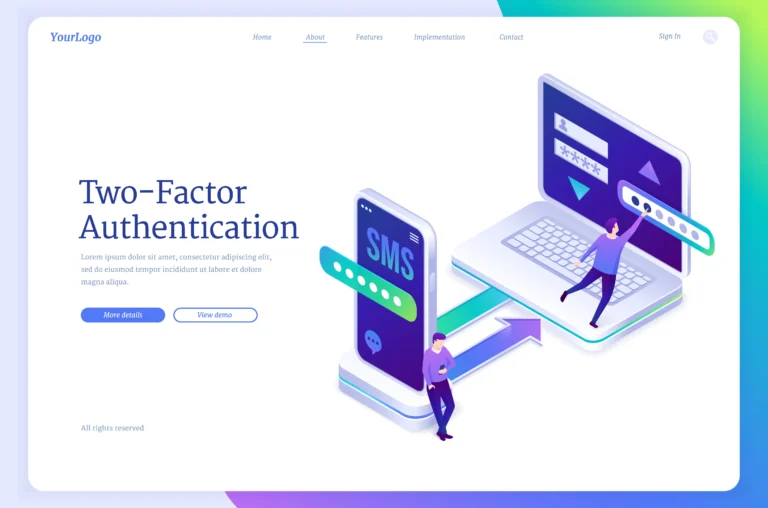
- Two-factor authentication
It simply means what it says on the tin: instead of utilizing just your username and password for authentication, there is a second stage in which you enter additional information. An SMS message sent to your phone number is part of the most widely used 2FA system. The system gives you a text message after you enter your login and password that contains a one-time password (OTP), which is often a six-digit numeric code that you must provide during the second authentication phase.
- Passphrases
In essence, phrases are just long passwords combined. You choose the phrase “SkyhighTEX fixed my issue” as your password rather than the word “Password,” which may be written as “SkyhighTEXfixedmyissue” if there are no spaces. The passphrase is more secure than the base password and easier to remember because of how long it is. Allowing for longer passwords in the future to accommodate passphrases is a relatively low-effort and inexpensive move toward greater security. Unfortunately, a lot of websites still only allow passwords with 12 characters.
- Single sign-on
Users of the single-sign-on system can access numerous different services using just one set of login information. All of the services’ ties of trust facilitate this. The SSO system passes tokens behind the scenes as you switch between secure sites to verify you have permission to enter each one.
- Passwordless
In place of being the complete digital security system, passwords are now its biggest risk. This has prompted many to believe that the future of passwords should involve their complete elimination. The revolution in passwordless access has been led by biometrics. Portable gadgets like smartphones are using fingerprint and/or facial recognition more and more.
- Zero login
Logins may be completely eliminated by some businesses. While your bank may actually call you if you attempt to log in from a different IP address, Amazon is currently testing systems that will continuously confirm your identity while you use their site by measuring your typing pressure and speed.
- Password managers
Using a password manager with sharing options is the best method to protect your IT infrastructure. Using two-factor authentication and high-level encryption, a password manager app ensures that only authorized users can decipher your passwords.
Conclusion
Passwords aren’t the best defense against online hackers and phishers, and they’re also difficult to administer, which is why they’ve fallen out of favor for a while. The majority of password-protected accounts advise users to build a complicated string of characters in their passwords to make them more difficult to decipher or hack. Creating a secure password is never simple. Most users use an easy-to-remember password because it is impossible to remember these complex ones.
Things are different with a passwordless system. Between any gadget and the internet, no information that can be read by humans is exchanged. Every exchange is encrypted. When your cellphone ends with a one-use code that could have only been generated by that phone, your identification is confirmed. Therefore, your device serves as your password.